DO NOT OPEN THE “LEGAL” PAGE
lemmy.world is a victim of an XSS attack right now and the hacker simply injected a JavaScript redirection into the sidebar.
It appears the Lemmy backend does not escape HTML in the main sidebar. Not sure if this is also true for community sidebars.

EDIT:
the exploit is also in the tagline that appears on top of the main feed for status updates, like the following one for SDF Chatter:
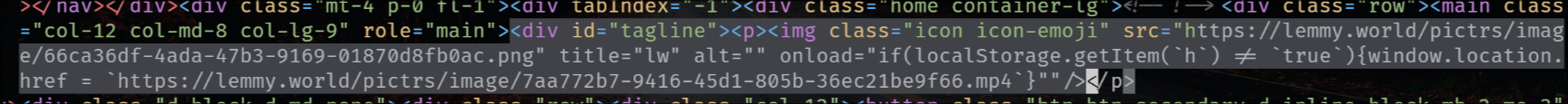
EDIT 2:
The legal information field also has that exploit, so that when you go to the “Legal” page it shows the HTML unescaped, but fortunately (for now) he’s using double-quotes.
"legal_information":" 


I can confidently say that in not a single company project I did frontend development for did I ever leave user input unsanitized.
But I did not ever create a Lemmy like project, that is true.
If you are doubting that this is one of the most frequently occurring security issues, I urge to search the web about it. It’s very easy to verify my claim.