DO NOT OPEN THE “LEGAL” PAGE
lemmy.world is a victim of an XSS attack right now and the hacker simply injected a JavaScript redirection into the sidebar.
It appears the Lemmy backend does not escape HTML in the main sidebar. Not sure if this is also true for community sidebars.

EDIT:
the exploit is also in the tagline that appears on top of the main feed for status updates, like the following one for SDF Chatter:
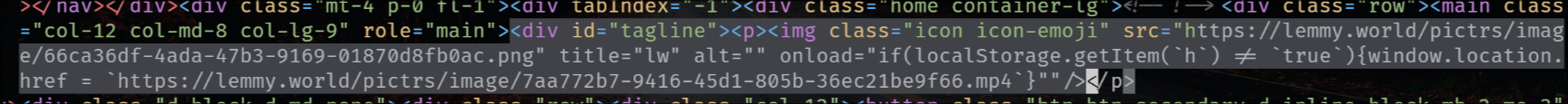
EDIT 2:
The legal information field also has that exploit, so that when you go to the “Legal” page it shows the HTML unescaped, but fortunately (for now) he’s using double-quotes.
"legal_information":" 


Not sanitizing user input is plain stupid. There is no excuse. Ever.
eval(input())
https://xkcd.com/327/
Exactly!
Show us your better Lemmy alternative then
“I don’t have to know how to pilot an helicopter to say that if it’s crashed on the ground, the pilot doon goofed”
The pilot crashed on the field because the helicopter was misfunctioning, and it risked falling on a primary school.
They probably don’t have one, but that doesn’t change the fact that not sanitizing user-input is still insane.
Mistakes happen. This is one of the most common vulnerabilities in the software world. Again, it’s easy to say it’s insane when you aren’t the one making it. I don’t see you making anything half as good and without mistakes.
Constructive criticism is okay, but this isn’t it. Sounds very entitled.
deleted by creator
It’s convenient to completely discredit a large piece of software taking years to develop as “insane” because they made a mistake (one of the most common security mistakes in the software world) when you don’t recognize the difficulty and wouldn’t be able to make something 10% as big.
And frankly it sounds silly.
The reason it’s perceived that way is because code injection in user input, is (one of) the most obvious, well-known, and easiest attacks to do, while at the same time being super easy to prevent.
It is one of the most well known, but it also is easy to miss, evidently from how often it happens despite it being very well known.
It’s very easy to fix once it’s known, but it is easy to go unnoticed.
Unless you somehow think that most app developers are incompetent, in which case I ask again: show me your better version.
I can confidently say that in not a single company project I did frontend development for did I ever leave user input unsanitized.
But I did not ever create a Lemmy like project, that is true.
If you are doubting that this is one of the most frequently occurring security issues, I urge to search the web about it. It’s very easy to verify my claim.
what about the time you wrote your “hello world” code? did you sanitize your user input then?
Simply having it Print “Hello World” without any user interaction? There are no user inputs to sanitize.
He sanitized the user input to the extreme by not allowing any.
The Apple school of thought
Best kind of correct
I mean if you’re gonna be making a literal english joke like this, then if there is no user input, then there is no user input to sanitize, which means no excuse is needed.
I follow and agree with your conclusion.
deleted by creator
“Listen here you little…”
Little Bobby Tables it is.